What Are Screen Time Restrictions?
Screen time restrictions are limits set on device use. They manage how long users can access certain apps and features. Parents often set these for their children. Companies also use them to maintain productivity. They can apply to all kinds of devices, like smartphones, tablets, and computers.
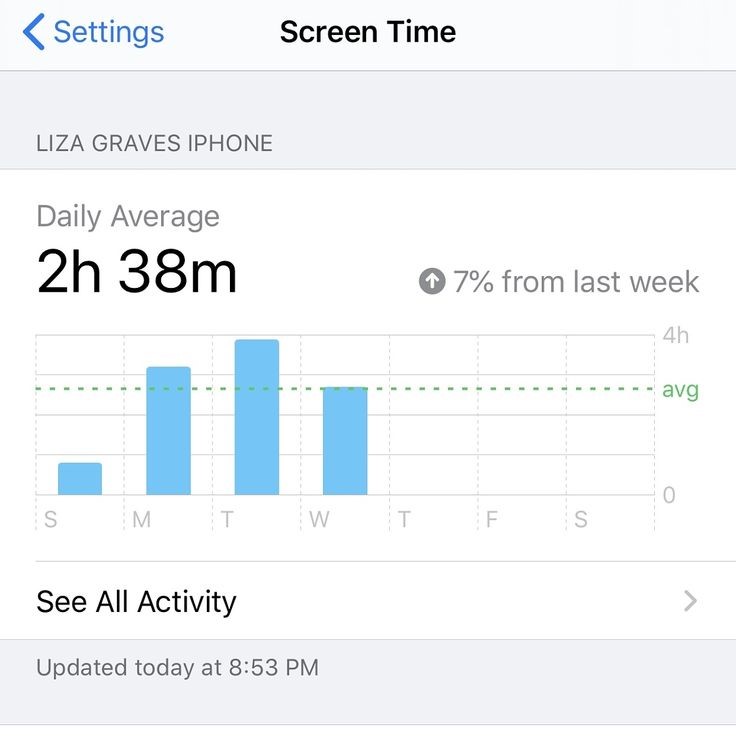
Restrictions serve multiple purposes. For kids, they help balance online activities with offline life. For adults, they can boost focus at work. These limits also support digital well-being. They encourage breaks and reduce the risk of screen addiction.
Devices like iPhones and Android phones have built-in restriction settings. Some apps offer similar functions. The goal is to control the time spent on screens. The settings might block apps or dim screens when the limit is reached. They may also require special passcodes to extend use.
Understanding screen time restrictions is the first step. This is crucial before learning how to bypass screen time. It’s important to know how restrictions work and why they are there. With this knowledge, users can consider if bypassing is the right choice.
Common Methods to Bypass Screen Time Limits
There are several known techniques to bypass screen time restrictions. These methods are mainly used when users feel the need to access their devices beyond the set limits. Here’s a rundown of common bypass strategies:
- Adjusting the device’s time and date: Some users manually change the time and date settings on their device to trick the system into believing it’s a different time, allowing more screen time.
- Factory resetting the device: This extreme method removes all data, including screen time restrictions, but also means losing all settings and personal information.
- Using a passcode: Those with knowledge of the device’s passcode can easily turn off or adjust screen time limits.
- Installing third-party apps: There are apps designed to help users get around screen time restrictions, but these can compromise device security.
- Finding software glitches: Sometimes software updates or system errors can be exploited to bypass restrictions, though this is not reliable or recommended.
Each of these methods comes with its own set of risks and considerations. It’s essential to weigh the pros and cons before attempting to bypass screen time limits. Future sections will discuss these aspects in detail.
Legal and Ethical Considerations
Before attempting to bypass screen time restrictions, users must consider legal and ethical aspects. These concerns can have long-lasting impacts.
- Respecting Parental Decisions: Parents set these limits for a reason. Often, it’s for their child’s safety and to instill discipline. Disregarding these measures can undermine parental efforts and trust.
- Workplace Policies: Companies enforce screen time rules to maintain productivity. Bypassing these can be a violation of work agreements. It could lead to disciplinary actions or even job loss.
- Terms of Service Agreement: Using devices means agreeing to the manufacturer’s terms. Tampering with device settings to bypass screen time may breach these terms. Users risk losing warranty coverage or support services.
- Moral Responsibility: There’s a moral obligation to use technology responsibly. Overriding restrictions promote a habit of circumventing rules that can extend to other areas of life.
- Encouraging Digital Addiction: Restrictions serve to prevent excessive screen time. Ignoring these can lead to unhealthy habits and contribute to digital addiction.
- Security Threats: Employing dubious methods to bypass limits may expose devices to security risks. These can include data theft or malware infections.
The legality and moral implications of bypassing screen time must not be taken lightly. Users should fully gauge the potential repercussions. A careful approach is necessary to make an informed decision.
Parental Controls vs. User Autonomy
When debating how to bypass screen time, one must consider the tension between parental controls and user autonomy. Parental controls are essential tools for guardians aiming to protect their children. They enforce beneficial limits on tech use, often in the child’s best interest. User autonomy, however, is about personal freedom over one’s digital activities.
- Parental Perspective: Parents implement screen time restrictions to safeguard children from online risks. They also foster time management skills through these controls.
- Child’s Viewpoint: Kids and teens may see restrictions as a hindrance to freedom. They might feel that their right to explore the digital world is limited.
- Balancing Act: Striking a balance is key. Users, especially younger ones, should learn self-regulation. At the same time, parents need to guide tech use wisely.
- Open Dialogue: Communication between parents and children is crucial. Discussing screen time rules can lead to mutual understanding and compromise.
Understanding the need for safety and the desire for independence can help in navigating these issues. Parents seek to strike a balance. They want to allow freedom but also protect their children. Kids and adolescents yearn to explore the digital space with fewer restrictions. The key to resolving this lies within respectful dialogue and setting reasonable boundaries. Acknowledging mutual concerns can pave the way toward a solution that respects both autonomy and safety.
 Step-by-Step Guide to Bypassing Restrictions
Step-by-Step Guide to Bypassing Restrictions
When considering how to bypass screen time, it is vital to understand each step involved. Here’s a simplified, step-by-step breakdown for those who decide to proceed, despite the potential risks. It’s important to remember that each device and software may have varying procedures, and users must proceed cautiously to avoid unintended consequences.
- Identifying the Restriction Type: Start by figuring out what kind of screen time restriction you are facing. Is it device-specific or app-specific?
- Researching Bypass Methods: Look up various methods applicable for your device or app. Ensure the information is current, as system updates can impact these techniques.
- Preparing the Device: Backup important data to prevent loss. Some bypass methods can reset your device or applications.
- Executing the Bypass: Choose the method that seems most appropriate for your needs. Whether it’s adjusting settings, using a passcode, or other tactics discussed earlier.
- Checking System Stability: After bypassing the restrictions, make sure the device operates normally. Keep an eye out for glitches that could indicate a problem.
- Restoring Data if Needed: If the process involved resetting your device, now’s the time to restore from the backup you created.
- Evaluating the Outcomes: Consider the repercussions, both immediate and long-term, of your actions. Reflect on the legal, ethical, and personal implications.
By following these steps, users can navigate through the process of how to bypass screen time restrictions. However, it’s worth reiterating that bypassing such limitations is not advised and should only be attempted with full awareness of the consequences.
Potential Risks and Consequences
Considering how to bypass screen time brings possible risks and consequences. It’s important to be aware of what might happen.
- Device Performance Issues: Techniques to bypass screen time can lead to device malfunctions. Users may experience slower operation or crashes.
- Data Loss: Some methods, like factory resetting, can erase everything. This includes contacts, photos, and messages. Always backup data before attempting methods.
- Warranty Voidance: Tampering with device settings could void the warranty. If problems arise, the costs are on you.
- Security Vulnerabilities: Third-party apps or exploiting glitches can expose your device. This may lead to hacking or malware. Protect device security at all times.
- Relationship Strain: For kids, bypassing parental controls can lead to trust issues. Respect family rules and discuss concerns instead of bypassing limits.
- Legal Issues: Some bypass methods can be illegal. Always check the laws and regulations before proceeding.
- Moral Considerations: Ignoring limits often feels easy. But it can start a habit of breaking rules. Reflect on what’s ethically right before deciding.
Considering these risks and consequences is essential. It helps make informed decisions about screen time usage. Think carefully about why and how you handle screen time restrictions.
Alternatives to Bypassing Screen Time
Instead of finding ways on how to bypass screen time, consider healthier alternatives. These can promote a balanced approach to device usage without the need for circumventing set limits. Here are some strategies that can serve as alternatives:
- Engage in offline activities: Pick up a new hobby or spend more time on existing interests. Engaging in sports, reading, or creative arts can reduce reliance on screens.
- Set personal goals: Aim for goals that require less screen time. This can turn attention from devices to personal achievement and growth.
- Use time management apps: Some apps help manage device use without disabling restrictions. They can encourage self-discipline in technology use.
- Device-free zones: Establish areas in the home where devices are not allowed. This can help create timeouts from digital exposure.
- Family agreements: Discuss and set screen time rules together. Family agreements on device usage help everyone to be on the same page.
By considering these alternatives, you can foster a sustainable and positive digital lifestyle. This also respects the intent behind screen time restrictions. Choose options that align with your need for balance between screen time and the rest of life’s activities.
 Safeguarding Against Bypass Techniques
Safeguarding Against Bypass Techniques
Parents and organizations invest in screen time restrictions for valid reasons. As such, it is crucial to know how to protect these settings from being bypassed. Safeguarding against bypass techniques involves several strategies.
- Update Regularly: Keep devices updated with the latest software. This closes security loopholes that may allow bypassing.
- Use Complex Passcodes: Opt for passcodes that are hard to guess. Change them often to stay ahead of savvy users who may try to crack them.
- Monitor Device Use: Pay attention to how devices are used. Look for signs of unusual activity that might suggest an attempt to bypass restrictions.
- Educate Users: Teach kids and employees about the dangers of bypassing screen time limits. Make them aware of the risks and consequences.
- Install Robust Security Apps: Choose security applications that offer additional protection. They can alert you to any attempts to disable restrictions.
- Restrict Installation of New Apps: Prevent the download of third-party apps that might help in circumventing screen time.
- Encourage Open Communication: Create an environment where children and employees feel comfortable discussing their screen time needs. This can reduce the desire to bypass limits.
Implementing these steps helps maintain the integrity of screen time restrictions. It upholds their purpose, which is to promote a healthy balance between digital and offline lives. Understanding and using these safeguards will make it less likely for users to seek out and use bypass strategies.
